- Generating Ssh Keys For Git On Windows
- What Are Ssh Keys
- Generating Ssh Keys For Gitlab
- Generating An Ssh Key Github
On Windows, you can create SSH keys in many ways. This document explains how to use two SSH applications, PuTTY and Git Bash.
Jun 22, 2012 Secure Shell (better known as SSH) is a cryptographic network protocol which allows users to securely perform a number of network services over an unsecured network. SSH keys provide a more secure way of logging into a server with SSH than using a password alone. With both Tectia SSH and OpenSSH servers, access to an account is granted by adding the public key to a /.ssh/authorizedkeys file on the server. To install the public key, Log into the server, edit the authorizedkeys file with your favorite editor, and cut-and-paste the public key output by the above command to the authorizedkeys file. If you use the Azure CLI to create your VM, you can optionally generate SSH public and private key files by running the az vm create command with the -generate-ssh-keys option. The keys are stored in the /.ssh directory. Note that this command option does not overwrite keys if they already exist in that location. Generating SSH Keys for Use with Automate Schedule File Transfer Systems Overview Automate Schedule allows secure file transfer protocol (SFTP) using public/private key encryption instead of a username/password combination.
2 days ago Tweet If you’re a developer, on devops or a system admin you probably use an SSH key to log into remote servers. I am typically on multiple projects at one time and some organizations require I generate a unique SSH key in order to work with them. PuTTYgen is an key generator tool for creating SSH keys for PuTTY. It is analogous to the ssh-keygen tool used in some other SSH implementations. The basic function is to create public and private key pairs. /windows-7-enterprise-activation-key-generator.html. PuTTY stores keys in its own format in.ppk files.
Joyent recommends RSA keys because the node-manta CLI programs work with RSA keys both locally and with the ssh agent. DSA keys will work only if the private key is on the same system as the CLI, and not password-protected.
PuTTY
PuTTY is an SSH client for Windows. You can use PuTTY to generate SSH keys. PuTTY is a free open-source terminal emulator that functions much like the Terminal application in macOS in a Windows environment. This section shows you how to manually generate and upload an SSH key when working with PuTTY in the Windows environment.
About PuTTY
PuTTY is an SSH client for Windows that you will use to generate your SSH keys. You can download PuTTY from www.chiark.greenend.org.uk.
When you install the PuTTY client, you also install the PuTTYgen utility. PuTTYgen is what you will use to generate your SSH key for a Windows VM.
Generating Ssh Keys For Git On Windows
| This page gives you basic information about using PuTTY and PuTTYgen to log in to your provisioned machine. For more information on PuTTY, see the PuTTY documentation |
|---|
Generating an SSH key
To generate an SSH key with PuTTYgen, follow these steps:
- Open the PuTTYgen program.
- For Type of key to generate, select SSH-2 RSA.
- Click the Generate button.
- Move your mouse in the area below the progress bar. When the progress bar is full, PuTTYgen generates your key pair.
- Type a passphrase in the Key passphrase field. Type the same passphrase in the Confirm passphrase field. You can use a key without a passphrase, but this is not recommended.
- Click the Save private key button to save the private key. You must save the private key. You will need it to connect to your machine.
- Right-click in the text field labeled Public key for pasting into OpenSSH authorized_keys file and choose Select All.
- Right-click again in the same text field and choose Copy.
Importing your SSH key

Now you must import the copied SSH key to the portal.
- After you copy the SSH key to the clipboard, return to your account page.
- Choose to Import Public Key and paste your SSH key into the Public Key field.
- In the Key Name field, provide a name for the key. Note: although providing a key name is optional, it is a best practice for ease of managing multiple SSH keys.
- Add the key. It will now appear in your table of keys under SSH.
/amazon-kindle-fire-5th-generation-enter-key.html. PuTTY and OpenSSH use different formats of public SSH keys. If the text you pasted in the SSH Key starts with —— BEGIN SSH2 PUBLIC KEY, it is in the wrong format. Be sure to follow the instructions carefully. Your key should start with ssh-rsa AAAA….
Once you upload your SSH key to the portal, you can connect to your virtual machine from Windows through a PuTTY session.
Git Bash
The Git installation package comes with SSH. Using Git Bash, which is the Git command line tool, you can generate SSH key pairs. Git Bash has an SSH client that enables you to connect to and interact with Triton containers on Windows.
To install Git:
- (Download and initiate the Git installer](https://git-scm.com/download/win).
- When prompted, accept the default components by clicking Next.
- Choose the default text editor. If you have Notepad++ installed, select Notepad++ and click Next.
- Select to Use Git from the Windows Command Prompt and click Next.
- Select to Use OpenSSL library and click Next.
- Select to Checkout Windows-style, commit Unix-style line endings and click Next.
- Select to Use MinTTY (The default terminal of mYSYS2) and click Next.
- Accept the default extra option configuration by clicking Install.
When the installation completes, you may need to restart Windows.
Launching GitBash
To open Git Bash, we recommend launching the application from the Windows command prompt:
- In Windows, press Start+R to launch the Run dialog.
- Type
C:Program FilesGitbinbash.exeand press Enter.
Generating SSH keys
First, create the SSH directory and then generate the SSH key pair.
One assumption is that the Windows profile you are using is set up with administrative privileges. Given this, you will be creating the SSH directory at the root of your profile, for example:
- At the Git Bash command line, change into your root directory and type.
Change into the .ssh directory
C:Usersjoetest.ssh- To create the keys, type:
- When prompted for a password, type apassword to complete the process. When finished, the output looks similar to:
Uploading an SSH key
To upload the public SSH key to your Triton account:
- Open Triton Service portal, select Account to open the Account Summary page.
- From the SSH section, select Import Public Key.
- Enter a Key Name. Although naming a key is optional, labels are a best practice for managing multiple SSH keys.
- Add your public SSH key.
When Triton finishes the adding or uploading process, the public SSH key appears in the list of SSH keys.
What are my next steps?
- Adding SSH keys to agent.
- Set up the Triton CLI and CloudAPI on Windows.
- Set up the Triton CLI and CloudAPI.
- Create an instance in the Triton Service Portal.
- Set up the
triton-dockercommand line tool. - Visit PuTTYgen to learn more about the PuTTYgen and to seethe complete installation and usage guide.
Overview
What Are Ssh Keys
Automate Schedule allows secure file transfer protocol (SFTP) using public/private key encryption instead of a username/password combination. To use this feature, you must create secure shell (SSH) keys that can be used by the SFTP client on the Automate Schedule agent.
Automate Schedule requires that private SSH keys be stored in OpenSSH (OpenBSD secure shell) format. On Windows, you can use PuTTYgen (www.putty.org) to generate the keys in the proper format. On UNIX and Linux, you can use ssh-keygen from OpenSSH (www.openssh.com). The following sections describe how to generate the SSH keys.
Windows
If you're currently using PuTTY for SFTP transfers from your Windows system, the auxiliary program, PuTTYgen, can be used to convert an existing key (that's saved in .ppk format) for use with Automate Schedule. Or PuTTYgen can be used to create a new key.
To convert an existing .ppk key to be compatible with Automate Schedule:
- Open PuTTYgen (PuTTY Key Generator).
- Click Load.
- Select your existing .ppk file and click Open.
- After the key is loaded, select Conversions > Export OpenSSH Key. This saves the private key to the correct file format for use with Automate Schedule.
- If there is a warning about saving without a passphrase, click Yes.
- Save the OpenSSH key in a location that can be accessed by the Automate Schedule jobs that will be using the key. A typical location for storing private keys like this would be in the user's home directory inside an .ssh directory. For example: 'c:usersmyuser.sshid_rsa'.
- Close PuTTYgen.
- When creating or editing a file transfer system object in Automate Schedule, select SFTP as the Protocol, select an Authentication Type of Public/Private Key, and reference the private key you just converted in the Private Key File Path on Agent. See the help on creating file transfer systems in Automate Schedule for more information.
To generate a new key that's compatible with Automate Schedule:
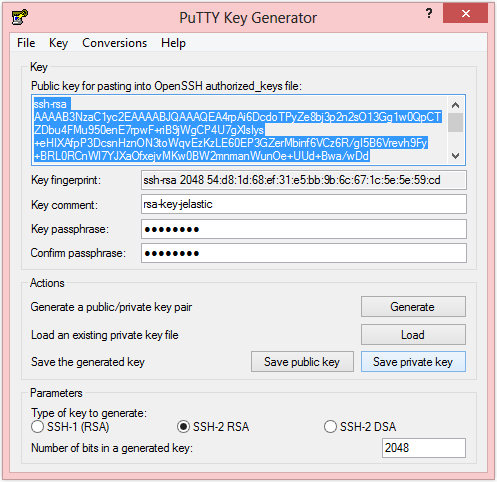
- Open PuTTYgen (PuTTY Key Generator).
- Select SSH-2 RSA in the Parameters section at the bottom of the page. Set the Number of bits in a generated key to '2048'.
- Click Generate. Move your mouse over the blank area in PuTTYgen to generate randomness for the key generation. The progress bar moves as you're moving the mouse.
After the key is generated, the public part of the key is displayed under Public key for pasting into authorized_keys file. This can be copied and pasted to the correct file on the server or copied and pasted into a text file that can be moved to the SSH server system. - Type a Key comment, if you want to save one with the new key.
- Optionally, type a Key passpharase. Type it again to confirm it.
- Select Conversions > Export OpenSSH Key. This saves the private key to the correct file format for use with Automate Schedule.
- If there's a warning about saving without a passphrase click Yes.
- Save the OpenSSH key in a location that can be accessed by the Automate Schedule jobs that will be using the key. A typical location for storing private keys like this would be in the user's home directory inside an .ssh directory. For example, 'c:Usersmyuser.sshid_rsa'.
- Close PuTTYgen.
- When creating or editing a file transfer system object in Automate Schedule, select SFTP as the Protocol, select an Authentication Type of Public/Private Key, and reference the private key you just converted in the Private Key File Path on Agent. See the help on creating file transfer systems in Automate Schedule for more information.
UNIX/Linux
UNIX and Linux users can use the OpenSSH program ssh-keygen to generate private/public keys. Private keys created by ssh-keygen can also be used on Automate Schedule Windows agents with no modification.
Generating Ssh Keys For Gitlab
To generate a new key that is compatible with Automate Schedule:
Generating An Ssh Key Github
- As the user who will be issuing SFTP requests from an Automate Schedule job on an agent, run the following command:
ssh-keygen -t rsa -b 2048 -f /home/myuser/.ssh/mykey
In this example, the private key will be stored in /home/myuser/.ssh/mykey and the public key will be stored in /home/myuser/.ssh/mykey.pub. - Optionally set a passphrase during key generation.
- When creating or editing a file transfer system object in Automate Schedule, select SFTP as the Protocol, select an Authentication Type of Public/Private Key, and reference the private key you just converted in the Private Key File Path on Agent. See the help on creating file transfer systems in Automate Schedule for more information.