This page, which requires that your browser support JavaScript(see Why JavaScript below),generates one-time pads or password lists in a variety offorms. It is based a high-quality pseudorandom sequencegenerator, which can be seeded either from the current dateand time, or from a seed you provide. Fill in the form belowto select the format of the pad and press “Generate” tocreate the pad in the text box. You can then copy and pastethe generated pad into another window to use as you wish.Each of the labels on the request form is linked to a descriptionof that parameter.
Two one-time pad generator programs are available at this site. The first is written in JavaScript embedded in a Web page. When you view the page with a JavaScript-capable browser, you can generate one-time pads to your specifications with all the computation done by the JavaScript interpreter built into the browser. One Time Pad is an easy to use personal encryption program using the elegant one time pad encryption technique. Great for students of cryptology or those who want to send encrypted messages.
Details
Each of the fields in the one-time pad request form is describedbelow.
Output
One Time Pad Cipher
Number of keys
Enter the number of keys you'd like to generate. If you generatemore than fit in the results text box, you can use the scrollbar to view the additional lines.
Line length
Lines in the output will be limited to the given length (or containonly one key if the line length is less than required for a singlekey). If the line length is greater than the width of the resultsbox, you can use the horizontal scroll bar to view the rest of theline. Enter 0 to force one key per line; this is handywhen you're preparing a list of keys to be read by a computer program.
Format
Key length
Each key will contain this number of characters, not countingseparators between groups.
Group length
If a nonzero value is entered in this field, the key will be brokeninto groups of the given number of characters by separators. Humansfind it easier to read and remember sequences of characters whendivided into groups of five or fewer characters.
Composition
Key text
This set of radio buttons lets you select the character set used inthe keys. The alternatives are listed in order ofincreasing security.
- Numeric
- Keys contain only the decimal digits “0” through “9”. Least secure.
- Word-like
- Keys are composed of alphabetic characters which obey the digraph statistics of English text. Such keys contain sequences of vowels and consonants familiar to speakers of Western languages, and are therefore usually easier to memorise but, for a given key length, are less secure than purely random letters.
- Alphabetic
- Keys consist of letters of the alphabet chosen at random. Each character has an equal probability of being one of the 26 letters.
- Gibberish
- Keys use most of the printable ASCII character set, excluding only characters frequently used for quoting purposes. This option provides the greatest security for a given key length, but most people find keys like this difficult to memorise or even transcribe from a printed pad. If a human is in the loop, it's often better to use a longer alphabetic or word-like key. Most secure.
Letters
The case of letters in keys generated with Word-like, Alphabetic, andGibberish key text will be as chosen. Most people find it easier toread lower case letters than all capitals, but for some applications(for example, where keys must be scanned optically by hardware thatonly recognises capital letters), capitals are required. Selecting“Mixed case” creates keys with a mix of upper- andlower-case letters; such keys are more secure than those with uniformletter case, but do not pass the “telephone test”: youcan't read them across a (hopefully secure) voice link without havingto indicate whether each letter is or is not a capital.
Random separators
When the Key length is longer thana nonzero Group length specification,the key is divided into sequences of the given group lengthby separator characters. By default, a hyphen, “-”, is usedto separate groups. If you check this box, separators will bechosen at random among punctuation marks generally acceptablefor applications such as passwords. If you're generating passwordsfor a computer system, random separators dramatically increasethe difficulty of guessing passwords by exhaustive search.
Include signatures
Download porting kit for mac. When this box is checked, at the end of the list of keys, preceded bya line beginning with ten dashes “-”, the 128 bit MD5 signature ofeach key is given, one per line, with signatures expressed as 32hexadecimal digits. Key signatures can be used to increase securitywhen keys are used to control access to computer systems or databases.Instead of storing a copy of the keys, the computer stores theirsignatures. When the user enters a key, its signature is computedwith the same MD5 algorithm used to generate it initially, and the keyis accepted only if the signature matches. Since discoveringa key which will generate a given signature is believed to becomputationally prohibitive, even if the list of signatures stored onthe computer is compromised, that information will not permit anintruder to deduce a valid key.
Signature calculation is a computationally intense process for whichJavaScript is not ideally suited; be patient while signatures aregenerated, especially if your computer has modestprocessing speed. Windows 7 professional 64 bit product key generator 2015.
For signature-based validation to be secure, it is essentialthe original keys be long enough to prohibit discovery of matchingsignatures by exhaustive search. Suppose, for example, one usedfour digit numeric keys, as used for Personal IdentificationNumbers (PINs) by many credit card systems. Since only 10,000different keys exist, one could simply compute the signatures ofevery possible key from 0000 through 9999, permitting an attacker whocame into possession of the table of signatures to recover thekeys by a simple lookup process. For maximum security, keys mustcontain at least as much information as the 128 bit signaturescomputed from them. This implies a minimum key length (not countingnon-random separator characters) for the various key formats asfollows:
| Key Composition | Minimum Characters |
|---|---|
| Numeric | 39 |
| Word-like | 30 |
| Alphabetic | 28 |
| Gibberish | 20 |
It should be noted that for many practical applications there is noneed for anything approaching 128-bit security. The guidelines aboveapply only in the case where maximum protection in the event ofundetected compromise of key signatures occurs. In manycases, much shorter keys are acceptable, especially when it is assumedthat a compromise of the system's password or signature database wouldbe only part of a much more serious subversion of all resourceson the system.
Seed
The seed is the starting value which determines allsubsequent values in the pseudorandom sequence used to generatethe one-time pad. Given the seed, the pad can be reproduced. Theseed is a 31-bit number which can be derived from the date andtime at which the one-time pad was requested, or from auser-defined seed value. If the user-defined seed consistsentirely of decimal digits, it is used directly as the seed,modulo 231; if a string containing non-digit charactersis entered, it is used to compute a hash code which isused to seed the generator.

When the clock is used to create the seed, the seed value is enteredin the User-defined box to allow you, by checking “User-defined”,to produce additional pads with the same seed.
Why JavaScript?
At first glance, JavaScript may seem an odd choice for programminga page such as this. The one-time pad generator program is ratherlarge and complicated, and downloading it to your browser takes longerthan would be required for a Java applet or to transfer aone-time pad generated by a CGI program on the Web server. I choseJavaScript for two reasons: security and transparency.
Security.The sole reason for the existence of one-time pads is toprovide a source of information known only to people to whomthey have been distributed in a secure manner. This meansthe generation process cannot involve any link whose securityis suspect. If the pad were generated on a Web server andtransmitted to you, it would have to pass over theInternet, where any intermediate site might make a copyof your pad before you even received it. Even if somemechanism such as encryption could absolutely prevent thepad's being intercepted, you'd still have no way to be surethe site generating the pad didn't keep a copyin a file, conveniently tagged with your Internet address.
In order to have any degree of security, it is essentialthat the pad be generated on your computer, withoutinvolving any transmission or interaction with othersites on the Internet. A Web browser with JavaScript makesthis possible, since the generation program embedded in thispage runs entirely on your own computer and does nottransmit anything over the Internet. Its output appearsonly in the text box, allowing you to cut and paste itto another application. From there on, its security isup to you.
Security is never absolute. A one-time pad generated withthis page might be compromised in a variety of ways, includingthe following:
- Your Web browser and/or JavaScript interpreter may contain bugs or deliberate security violations which report activity on your computer back to some other Internet site.
- Some other applet running on another page of your browser, perhaps without your being aware of its existence, is spying on other windows.
- Some other application running on your computer may have compromised your system's security and be snooping on your activity.
- Your Web browser may be keeping a “history log” or “cache” of data you generate. Somebody may come along later and recover a copy of the pad from that log.
- The implementation of this page may contain a bug or deliberate error which makes its output predictable. This is why transparency, discussed below, is essential.
- Your computer's security may have been compromised physically; when's the last time you checked that a bug that transmits your keystrokes and/or screen contents to that white van parked down the street wasn't lurking inside your computer cabinet?
One can whip oneself into a fine fever of paranoia worrying aboutthings like this. One way to rule out the most probable risksis to download a copy of the generator page and run itfrom a “file:” URL on a computer which has no networkconnection whatsoever and is located in a secure locationunder your control. And look very carefully at any filescreated by your Web browser. You may find the most interestingthings squirreled away there….
Transparency.Any security-related tool is only as good as its designand implementation. Transparency means that, inessence, all the moving parts are visible so you can judgefor yourself whether the tool merits your confidence. Inthe case of a program, this means that source code mustbe available, and that you can verify that the programyou're running corresponds to the source code provided.
The very nature of JavaScript achieves this transparency.The program is embedded into this actual Web page; toexamine it you need only use your browser's “View Source”facility, or save the page into a file on your computerand read it with a text editor. JavaScript's beingan interpreted language eliminates the risk of your runninga program different from the purported source code: withan interpreted language what you read is what you run.
Transparency is important even if you don't know enough aboutprogramming or security to determine whether the programcontains any flaws. The very fact that it can be examinedby anybody allows those with the required expertise to passjudgement, and you can form your own conclusions based ontheir analysis.
Credits
The pseudorandom sequence generator is based on L'Ecuyer'stwo-sequence generator as described inCommunications of the ACM, Vol. 31 (1968), page 742.A Bays-Durham shuffle is used to guard against regularitieslurking in L'Ecuyer's algorithm; seeACM Transactions on Mathematical Software, Vol. 2 (1976)pages 59–64 for details.
The JavaScript implementation of theMD5 message-digest algorithmwas developed by Henri Torgemane; please view the source code of thispage to examine the code, including the copyright notice andconditions of use. The MD5 algorithm was developed by Ron Rivest.
by John WalkerMay 26, 1997
Updated: November 2006
This document is in the public domain.
Introduction
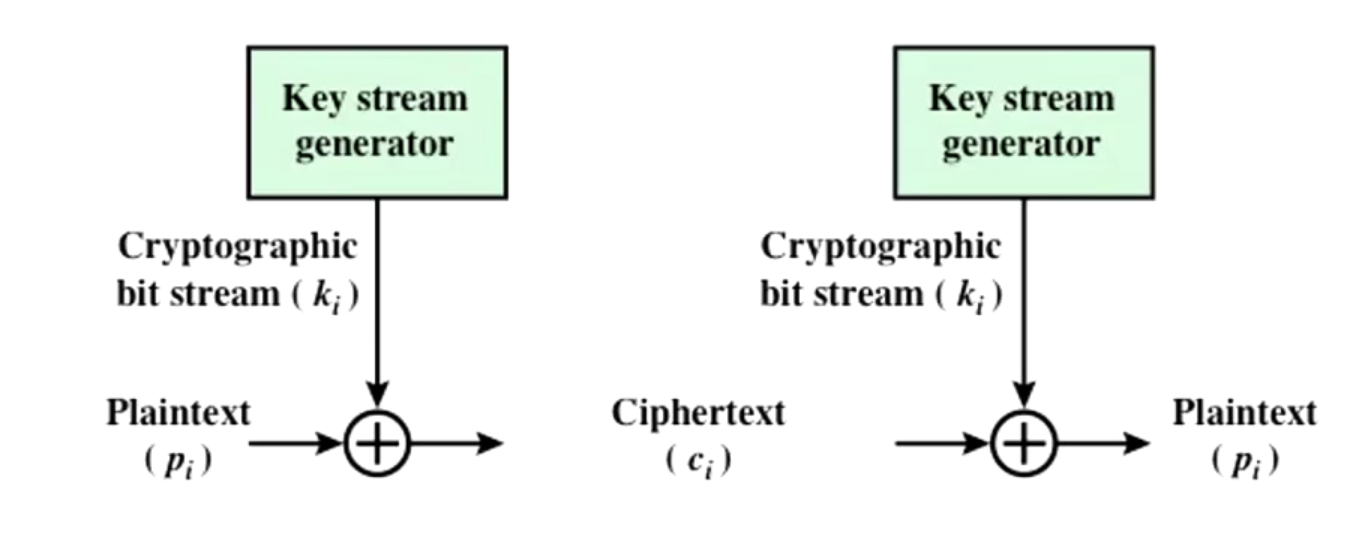
Systems which use passwords and/or encryption keys toauthenticate an individual's identity or protect againstinterception of communications achieve the highest degree ofsecurity when each password or key is used only once. Spies arefurnished “one-time pads” containing pages of keys used toencrypt individual characters of secret messages, then discarded.As long as the physical security of the two copies of a one-timepad is assured and the keys on the pad are sufficiently random,security is absolute.
Swiss banks which accept electronic payment orders use a similarmechanism to verify the identity of the issuer of an order. Whena client authorises the bank to accept electronic orders, thebank delivers, by registered mail, a list of individual sessionpasswords (usually numbers of 4 to 6 digits). The customeragrees to keep the list of passwords physically secure, and tonot hold the bank liable if the customer allows the list to fallinto unauthorised hands. Each time an order is given, inaddition to the regular user identity and password, the next keyfrom the list must be entered, and then crossed off by the user.The bank verifies the key against a copy of the list stored intheir own secure computer, and only if the key matches is theorder accepted. Multiple incorrect entries block electronicaccess to the customer's account until re-enabled by the customerproviding suitable verification that an unauthorised accessattempt did not, in fact, occur.
Note that even if the customer's entire communication sessionwith the bank is intercepted, the eavesdropper will not be ableto subsequently issue orders in the customer's name since theone-time password used in the compromised session will never beused again, and provides no usable clue as to subsequent one-timepasswords.
A choice of programs
Two one-time pad generator programs are available at thissite. The first is written in JavaScriptembedded in a Web page. Whenyou view the page with a JavaScript-capable browser,you can generate one-time pads to your specificationswith all the computation done by the JavaScript interpreterbuilt into the browser. Since the contents of the pad neverpasses over the Internet, you don't have to worry aboutit being intercepted. Other security issues are discussedin the generator page.
A second one-time pad generator is implemented in C for Unix systems. (With a little fiddling it can be gotten to work on MS-DOS or othersystems with a C compiler and library that more-or-less emulates Unix,and a ready-to-run 32-bit Windows console application is included.) It is available for downloading as a gzipped TARarchive and documented in an included manual page, which you canalso read on-line.
JavaScript One-time Pad Generator
C Language One-time Pad Generator Program
by John WalkerFebruary, 1996
Updated: May 1997
Updated: November 2006
Updated: June 2012
One Time Pad Key Generator Download
Message Authentication Codes
Updated: June 2014Top News
- ✔ August Smart Lock 2nd Generation Virtual Key
- ✔ Iobit Malware Fighter 6 Pro Key Generator
- ✔ Openssl Generate Public And Private Key
- ✔ Microsoft Office Product Key 2016 Generator
- ✔ Microsoft Office 365 Product Key Generator 2018
- ✔ Generate Rs256 Public Private Key
- ✔ Generate New Django Secret Key
- ✔ Parallels Activation Key Generator Mac
- ✔ Avg Pc Tuneup 2013 License Key Generator
- ✔ Reimage Pc Repair License Key Generator Plus Crack Download